Vibes into Workflows: Leveraging Vibe Coding and Low-Code for Rapid Internal Tool Development in 2026
For decades, the “Internal Tool Bottleneck” has been a fixture of corporate life. A department needs a simple dashboard to track vendor spend or a custom tool to automate employee onboarding, but the request languishes in the IT backlog for six months. In 2026, this bottleneck has finally cleared. The solution wasn’t hiring more engineers—it was the rise of Vibe Coding.
By shifting the focus from syntax to intent, Vibe Coding allows operators, product managers, and developers to “vibe” functional applications into existence through natural language dialogue, effectively ending the era of Shadow IT by making official development faster than unapproved workarounds.
Defining Vibe Coding: The Intent-First Era
While Low-Code platforms (like Power Apps or Appsmith) utilize visual drag-and-drop blocks to represent logic, Vibe Coding is Intent-First. Coined by AI pioneers in 2025 and matured in 2026, vibe coding describes a workflow where the “builder” describes a desired … Read More
Transitioning from Traditional Coding to Intent-Driven Software Development with AI
For decades, the life of a software engineer was defined by the “imperative”—the meticulous process of telling a computer exactly how to do something. We wrote every loop, managed every memory allocation, and debugged every semicolon. But as we move into 2026, the bedrock of the industry is shifting. We are entering the era of Intent-Driven Development, where the focus has moved from technical instruction to high-level orchestration.
In this new paradigm, the “code” is no longer the product; the “intent” is. Here is how the transition is reshaping the very fabric of software engineering.
1. The Death of Syntax, the Birth of Intent
In the traditional era, a developer’s value was often tied to their mastery of a specific syntax. Knowing the quirks of C++ or the nuances of React was a barrier to entry. Today, Large Language Models (LLMs) have effectively commoditized syntax.
Intent-Driven Development allows us … Read More
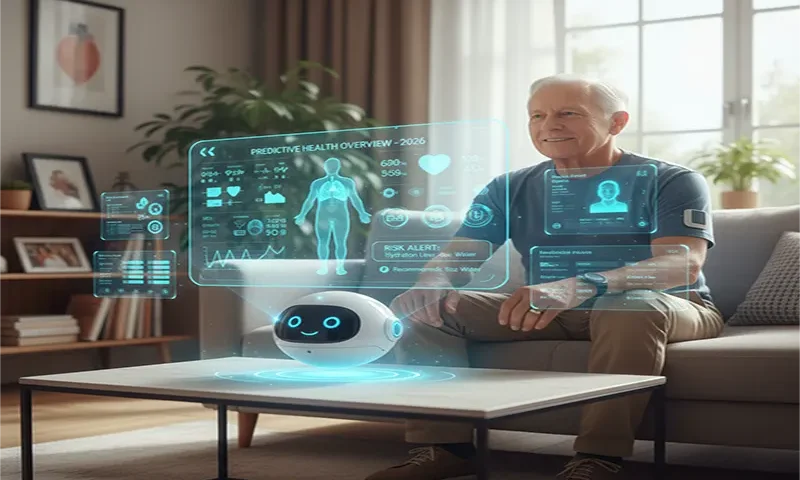
The Guardian in the Living Room: Multimodal AI Agents for Predictive Chronic Disease Management at Home in 2026
For decades, chronic disease management was a game of “catch-up.” A patient with heart failure would wait for overt symptoms—shortness of breath or swollen ankles—before seeking care, often resulting in an expensive emergency room visit. By 2026, the paradigm has shifted. The “Hospital-at-Home” model has matured from a pilot project into a global standard, powered by Multimodal AI Agents. These are not mere monitoring tools; they are autonomous digital guardians that fuse disparate data streams to predict clinical decline days before a patient even feels unwell.
Beyond Single-Stream Data: The Power of Sensor Fusion
In 2024, remote monitoring was often limited to single-parameter alerts—a “high heart rate” or “low oxygen” notification. In 2026, Multimodal AI leverages Sensor Fusion to create a high-definition picture of patient health. By correlating physiological, behavioral, and environmental data, these agents detect cross-parameter interactions that humans might miss.
Multimodal Data Fusion: From Modality to Clinical
… Read MoreEfficiency Benefits of Tandem Perovskite-Silicon Solar Cells for Portable Power
In the race to decarbonize our energy grid, the humble silicon solar cell has been the workhorse for over half a century. However, as of early 2026, the industry has hit a wall. Traditional single-junction silicon cells are rapidly approaching their theoretical “Shockley-Queisser” limit of approximately 29%. To push further—especially for the demanding world of portable power where every gram of weight and every square centimeter of space matters—we must look to the “Tandem” revolution.
The integration of perovskite and silicon into a single, stacked device is not just an incremental improvement; it is a fundamental leap that is redefining what “off-grid” power looks like.
1. Breaking the Shockley-Queisser Limit
The primary limitation of silicon is its fixed bandgap of roughly 1.12 eV. This means it is highly efficient at capturing red and infrared light but loses the energy of high-energy blue and ultraviolet (UV) photons as waste heat.… Read More
The Lean Machine: Implementing Frugal AI and Right-Sized Models for Small Business Efficiency
In the early days of the AI boom, the prevailing wisdom was “bigger is better.” Enterprises raced to integrate the largest, most expensive models available, often using a massive 400B+ parameter model to perform tasks as simple as summarizing an internal email. By 2026, however, the “AI Arms Race” has matured into the Efficiency Era.
For small businesses, the competitive edge no longer comes from having the largest AI, but from implementing Frugal AI: a strategy centered on high-performance, Right-Sized Models that provide 95% of the utility at less than 5% of the cost.
The Fallacy of “Bigger is Better”
The most significant drain on small business AI budgets in 2025 was “Over-Provisioning.” Using a frontier model like GPT-4o or Claude 3 Opus for routine data entry is like using a rocket ship to go to the grocery store.
In 2026, small businesses are embracing the Latency-Cost-Accuracy Triangle… Read More